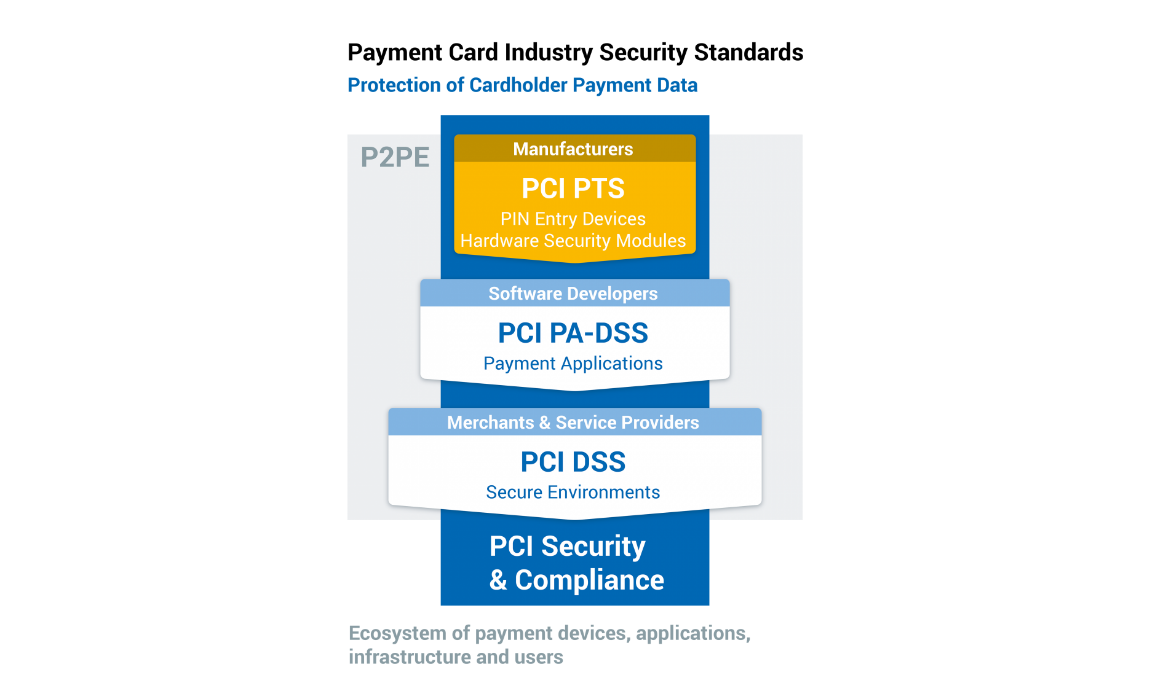
The Payment Card Industry Data Security Standard (PCI DSS) defines a set of security standards to ensure companies that accept, process, store or transmit credit/debit card information maintain a secure environment and protects cardholder against misuse of their personal information.
One of the most efficient ways of complying with PCI DSS is to use HSMs.
Overview

PCI Data Security Standard (PCI DSS)
The PCI DSS is an overarching standard that applies to all entities that store, process, and/or transmit cardholder data. It covers technical and operational components that are included in or connected to the systems that touch cardholder data. If you accept or process payment cards in any shape or form, you must follow the standards defined in PCI DSS.

PIN Transaction Security (PTS) Requirements
The PCI PTS is a set of security requirements that applies to the manufacturers who manufacture devices used for payment card financial transactions. The requirements are for manufacturers to follow in the design, manufacture and transport of a device to the entity that implements it. Financial institutions, processors, merchants and service providers should only use devices or components that are tested and approved by the PCI SSC.

Payment Application Data Security Standard (PA-DSS)
The PA-DSS is for software vendors and others who develop payment applications that store, process or transmit cardholder data and/or sensitive authentication data. Most card brands encourage merchants to use payment applications that are tested and approved by the PCI SSC.

Hardware Security Module (HSM) and PCI
All Payment HSM vendors must comply to the standards defined in PCI PTS HSM to be able to design a compliant and secure Hardware security module and process payment transactions. A PCI PTS certified HSM is the key to allow its users achieve PCI DSS compliance.
The PCI PTS HSM standards are categorized in two sections, Physical and Logical Security. Some requirements that defines the physical security of the HSM are derived from requirements in Federal Information Processing Standard 140-2 (FIPS 140-2). The certification ensures an active tamper response mechanism to zeroize secret and private keys during a penetration and side-channel attack.
The PCI HSM standard covers the lifecycle of the HSM up to the point of its first delivery to the initial point of deployment facility. Subsequent stages of the HSM’s lifecycle continue to be of interest to PCI and are controlled by other PCI standards.
The PCI HSM security requirements are derived from existing ISO, ANSI, and NIST standards; and accepted/known good practice recognized by the financial payments industry. The requirements are classified in four different Evaluation Domains:
- Evaluation Module 1 – This module defines core security requirements including Physical and Logical security of the HSM along with policies and procedures that must be followed.
- Evaluation Module 2 – This module defines Key-Loading procedures and devices used to load keys in the HSM.
- Evaluation Module 3 – This module covers the remote administration aspect of the HSM.
- Evaluation Module 4 – This module covers device security requirements during manufacturing and between manufacturer and point of initial deployment.
Utimaco HSMs and PCI Compliance
The Utimaco HSMs are designed on the basic principles defined by PCI Council, ISO, NIST and ANSI. This includes our Atalla AT1000 and PaymentServer.